aws-ket
Utility tool to encrypt data using AWS KMS and store it in preferred backend.
Overview
AWS-KET (AWS KMS Encryption Tool) uses AWS KMS Key to encrypt and decrypt files/contents based on user provided kms keys and push them to a datastore backend (S3, RDS or DynamoDB).
Setup
This application will only work if you have AWS account with full privileges on KMS and S3 services in AWS. You should also have aws cli tool installed.
Note: Currently this tool only uses AWS region us-east-2 for usage of kms and s3.
Using Source Code
Initaliztion of app
git clone git@github.com:sayefiqb/aws-ket.git
cd awsket
python init.py
Encrypt text/file
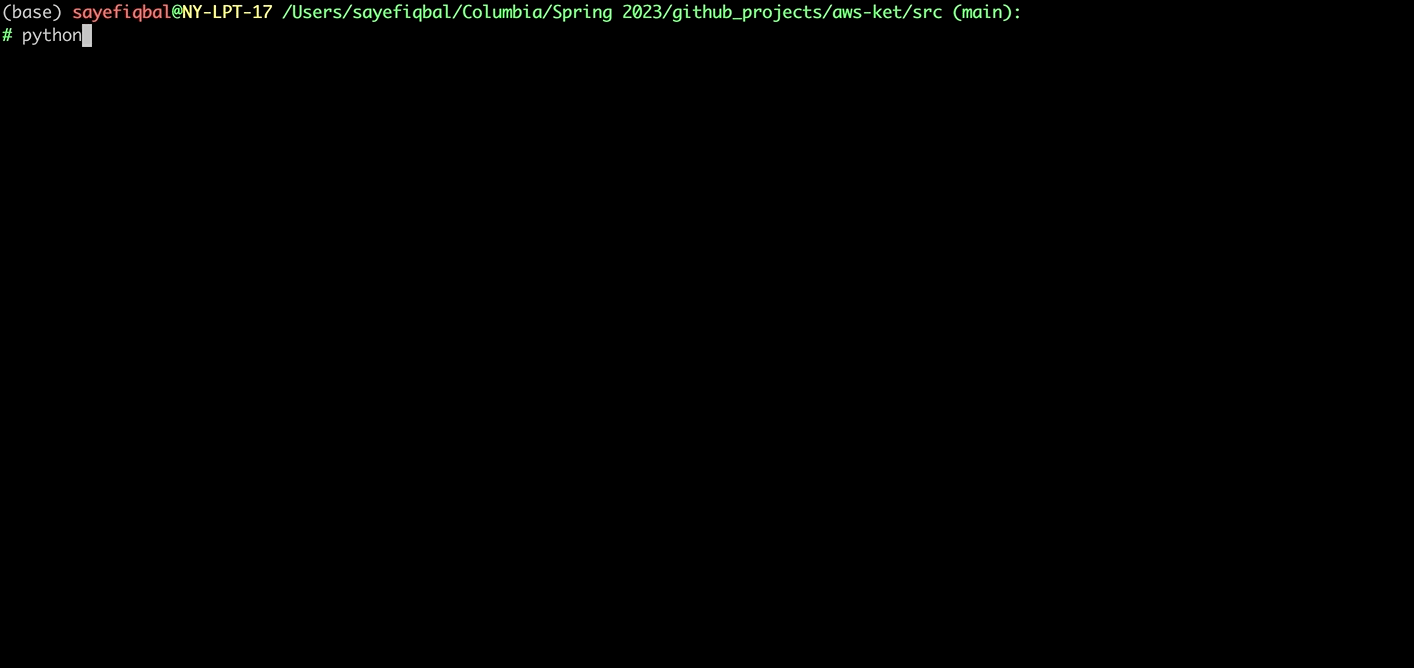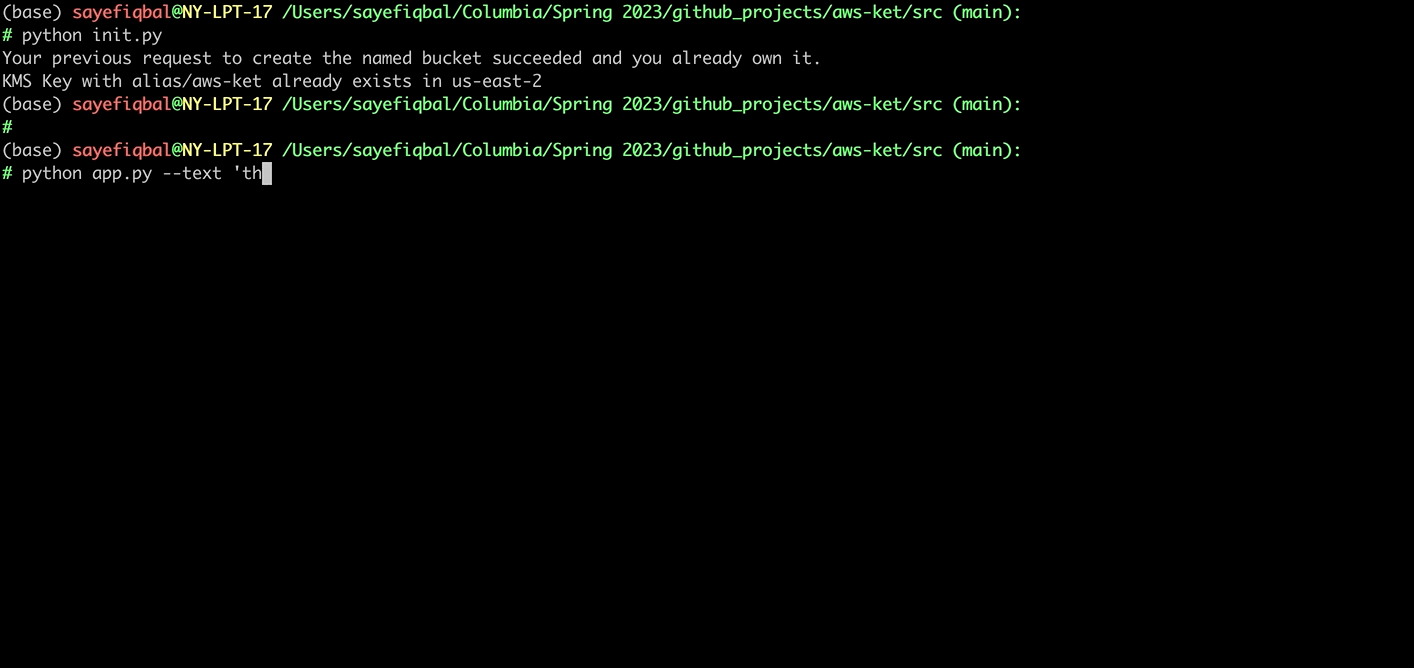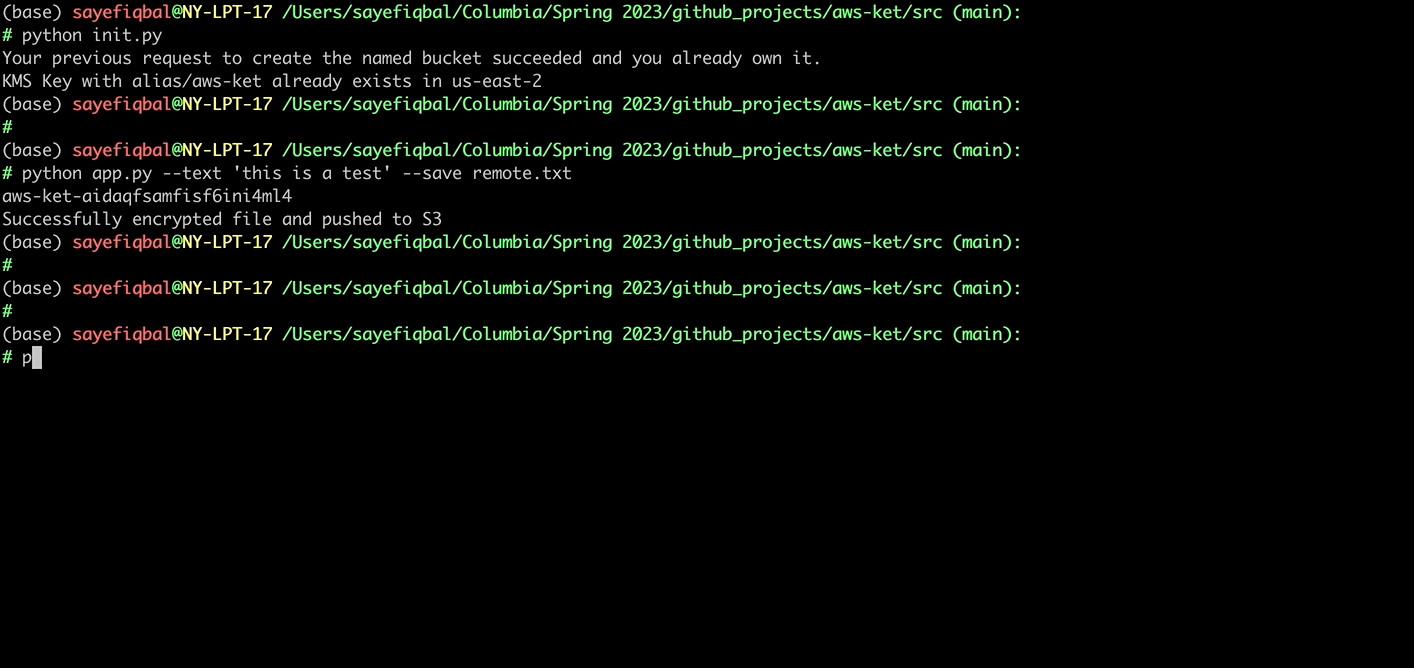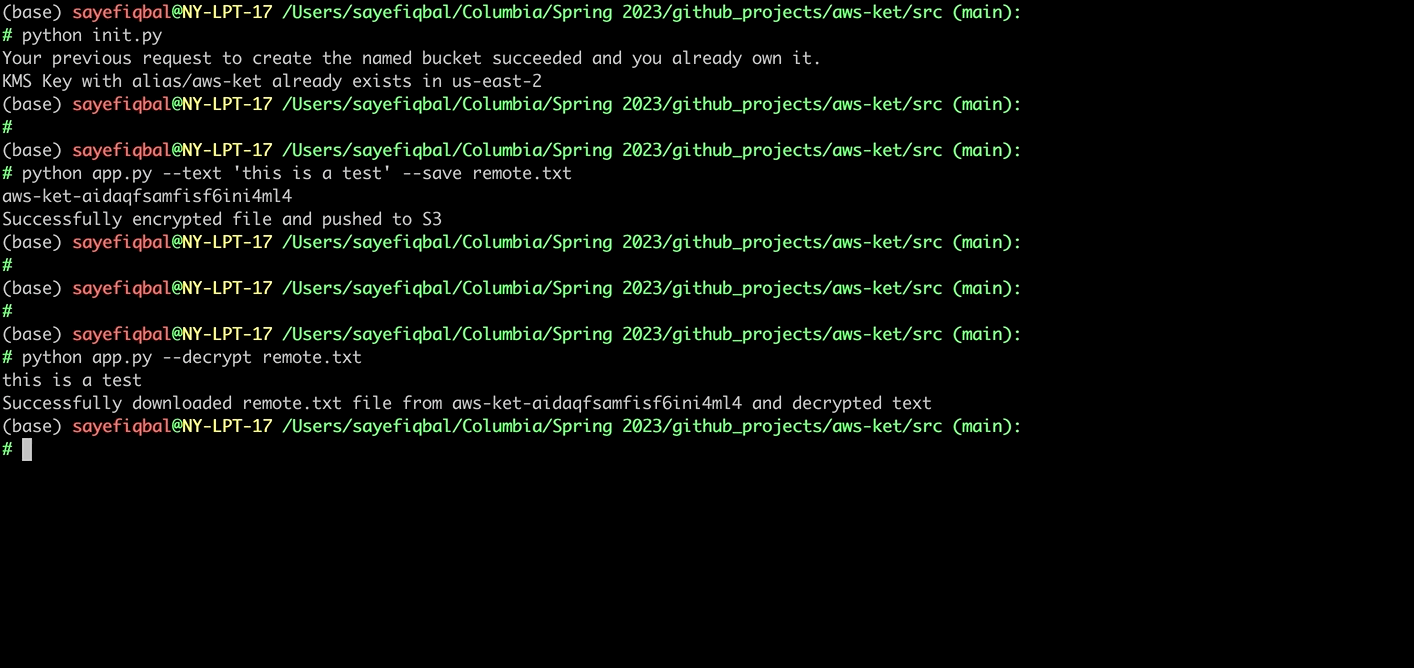
python app.py --text <TEXT_TO_ENCRYPT> --save <FILE_NAME_IN_S3>
python app.py --file <PATH_OF_FILE_TO_ENCRYPT> --save <FILE_NAME_IN_S3>
Decrypt text/file from S3
This will save with same name as remote
python app.py --decrypt <FILE_NAME_IN_S3>
OR
To specify name for saved file
python app.py --decrypt <FILE_NAME_IN_S3> --save <FILE_NAME_TO_SAVE_AS_IN_LOCAL>
Cleanup
To cleanup your S3 bucket and start over
python cleanup.py
Using Library form Pypi
pip install aws-ket
Initaliztion of app
from awsket import ket
AWS_REGION = 'us-east-2'
KMS_ALIAS = 'alias/aws-ket'
user_name = ket.get_iam_user()['UserId'].lower()
bucket_name = f'aws-ket-{user_name}'
ket.create_s3_bucket(bucket_name, AWS_REGION)
alias_name = ket.check_alias(KMS_ALIAS, AWS_REGION)
kms_key_id = ket.create_kms_key(AWS_REGION)
alias_name = ket.create_kms_alias(kms_key_id, KMS_ALIAS, AWS_REGION)
Encrypt text
from awsket import ket
AWS_REGION = 'us-east-2'
KMS_ALIAS = 'alias/aws-ket'
TEXT = 'This is a sample text for testing encryption! Happy coding :)'
FILE = 'EXAMPLE.txt'
user_name = ket.get_iam_user()['UserId'].lower()
bucket_name = f'aws-ket-{user_name}'
encrypted_string = ket.encrypt_text(KMS_ALIAS, TEXT, AWS_REGION)
ket.push_to_s3(bucket_name, FILE, encrypted_string, AWS_REGION)
Decrypt text
from awsket import ket
AWS_REGION = 'us-east-2'
KMS_ALIAS = 'alias/aws-ket'
FILE = 'EXAMPLE.txt'
user_name = ket.get_iam_user()['UserId'].lower()
bucket_name = f'aws-ket-{user_name}'
decrypted_text = ket.decrypt_text(bucket_name, FILE, KMS_ALIAS, AWS_REGION)
print(decrypted_text)
Details
This project uses Makefile as a command registry, with the following commands:
make: list available commandsmake develop: install and build this library and its dependencies usingpipmake lint: perform lint usingblackmake scan: run static analysis on code usingflake8make test: run automated tests withpytestmake coverage: run automated tests withpytestand collect coverage information
coverage output can also be found in html format in htmlcover directory.
Example
First download the source code